Secure your compute instances, whether they are in your data center or the public cloud
- Application Security
- Cloud Security
- Network Security
- Security Assessments
- Unified Security Platform
- Secure Mobility And VPN
Cisco Tetration
Applications are increasingly dictating the scale and design of data center infrastructure. Today’s applications are dynamic, using virtualization, containerization, microservices, and workload mobility technologies, with communication patterns between application components constantly changing. Now, 76 percent of data center traffic is east-west, a fundamental change from traffic patterns in the past. This technological shift has contributed to an increased attack surface causing network and security operations issues in their ability to implement a secure infrastructure.
”Cisco’s Tetration Analytics has provided us with unprecedented visibility into our network and applications and is enabling us to migrate from a legacy policy model to a significantly more secure policy model driven by ACI.
Healthcare customer

Application Security
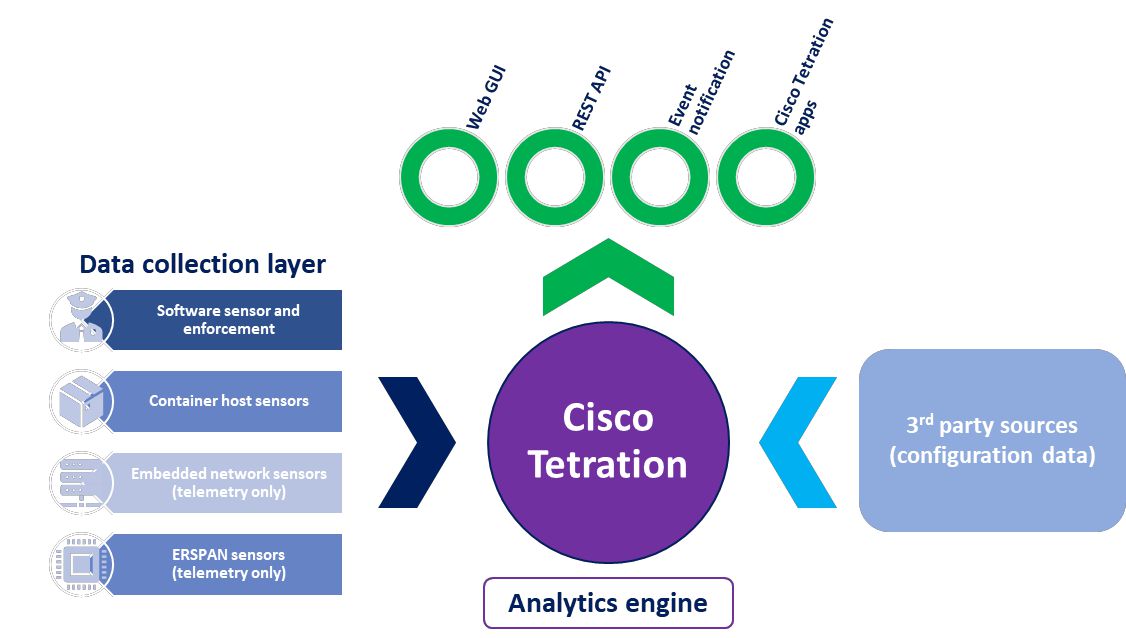
Cisco Tetration platform
The Cisco Tetration platform addresses these requirements using unsupervised machine learning, behaviour analysis, and algorithmic approaches. It provides a ready-to-use solution to accurately identify applications running in the data center and their dependencies and the underlying policies between different application tiers. The platform is also designed to implement a zero-trust model using allow/block policies and segmentation, monitor the behaviour of the processes running on the servers, and identify software-related vulnerabilities and exposures.
Together We Build Dreams
Ready To See What's Next?
Make informed security and operational decision using behavior analysis.
Get in touch with us to see how Tetration can protect your mission-critical applications with microsegmentation.

